Technical Aspects of Threats and Vulnerabilities
Key Takeaways & Definition
- ● Core Definition: A Threat is a potential cause of harm; a Vulnerability is a weakness that can be exploited.
- ● The Golden Formula:
Risk = Threat × Vulnerability - ● Key Takeaway: You cannot control all threats (external hackers), but you can control vulnerabilities (patching software, using firewalls).
Introduction to Threats and Vulnerabilities
Cybersecurity is fundamentally a race between defenders closing gaps and attackers finding them. Understanding the technical distinction between a "Threat" and a "Vulnerability" is the first step in securing any network. If a system has no vulnerabilities, a threat cannot harm it. Conversely, a vulnerability is harmless if no threat exists to exploit it.
Security Threats
Definition of Security Threat
A security threat is any potential malicious act that attempts to gain access to a computer network without authorization, typically to destroy data, steal information, or disrupt digital life. Threats can be intentional (hackers) or accidental (natural disasters).
Types of Security Threats
Threats are broadly categorized into Structured Threats (planned attacks by skilled hackers) and Unstructured Threats (accidental or amateur attacks).
Classification of Cyber Threats
From a technical perspective, threats are classified by their vector (method of delivery):
Malware-Based Threats
Malicious software designed to infiltrate systems:
- ● Ransomware: Encrypts files and demands payment for decryption.
- ● Trojans: Disguised as legitimate software to gain access.
- ● Spyware: Monitors user activity without consent.
Network-Based Threats
Attacks targeting network infrastructure (defending against these is covered in Firewall):
- ● DoS/DDoS Attacks: Flooding bandwidth to overwhelm servers (attacks Availability).
- ● Packet Sniffing: Intercepting unencrypted data in transit (attacks Confidentiality).
Web Application Threats
Attacks targeting websites (attacks Integrity):
- ● SQL Injection: Manipulating database queries via malicious input.
- ● Cross-Site Scripting (XSS): Injecting malicious scripts into web pages.
Social Engineering Threats
Attacks that manipulate human psychology rather than technology (e.g., Phishing emails).
Insider Threats
Malicious or negligent actions by employees who have authorized access to the system.
Security Vulnerabilities
Definition of Vulnerability
A vulnerability is a flaw, loophole, or weakness in a system's design, implementation, or operation and management that could be exploited to violate the system's security policy.
Sources of Vulnerabilities
- ● Complexity: The more code a program has, the more likely it is to have errors.
- ● Familiarity: Common code (like Windows OS) is well-known to hackers, making it a frequent target.
- ● Connectivity: Physical ports and wireless connections increase the number of entry points.
- ● Poor Password Management: Weak or default passwords are the most common vulnerability.
Types of Vulnerabilities (Technical)
Software Vulnerabilities
Bugs in the code, such as unvalidated input fields allowing SQL injection.
Hardware Vulnerabilities
Physical weaknesses, such as unprotected USB ports or side-channel attacks (like Spectre/Meltdown).
Network Vulnerabilities
Misconfigured firewalls, open ports, or weak Wi-Fi encryption (WEP).
Configuration Vulnerabilities
Using default settings (e.g., leaving the admin password as "admin").
Zero-Day Vulnerabilities
A flaw that is unknown to the software vendor. Hackers exploit it before a patch is available (hence "zero days" to fix it).
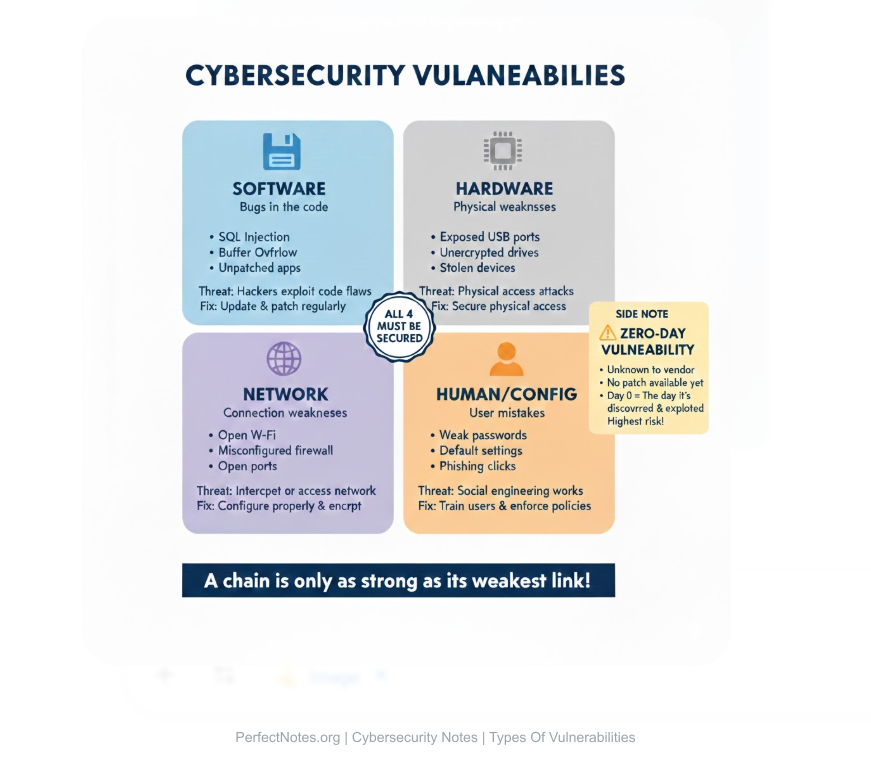
⚠️ Common Technical Vulnerabilities (OWASP Focus)
When analyzing technical risks, always check for these specific weaknesses:
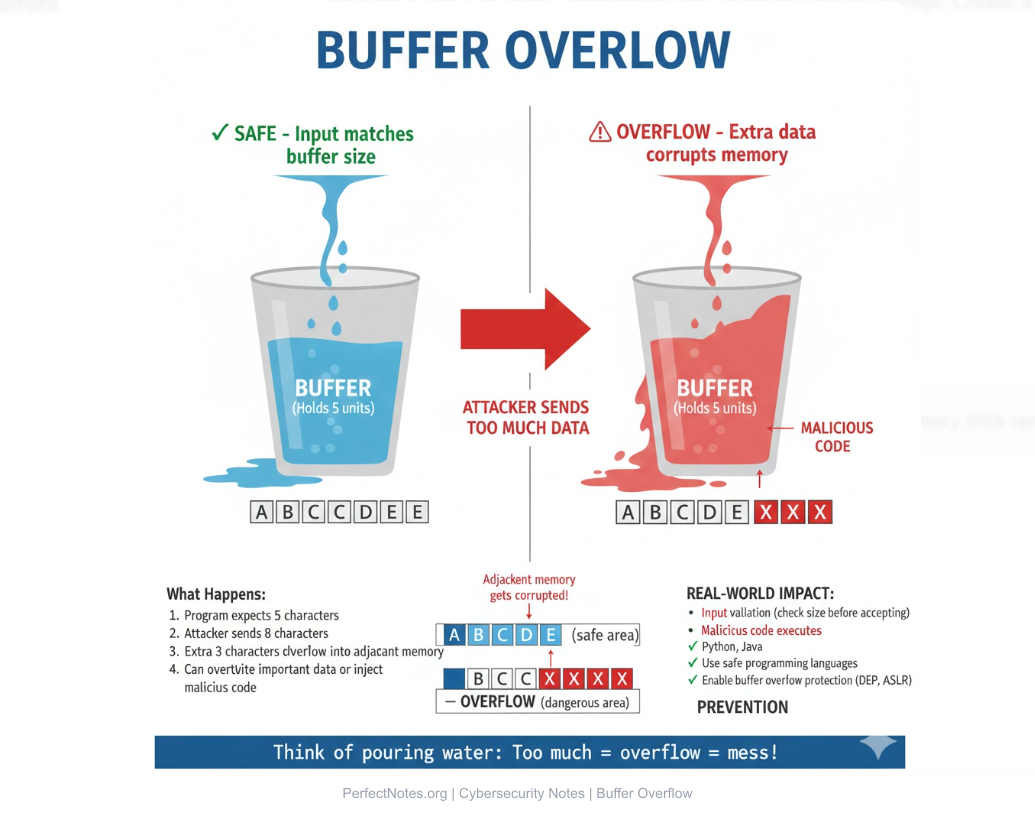
- ● Buffer Overflow: When a program writes more data to a buffer (memory block) than it can hold, overwriting adjacent memory. This can crash the system or execute malicious code.
- ● Race Conditions: When a system attempts to perform two or more operations at the same time, but because of the nature of the device or interface, the operations must be done in the proper sequence.
- ● Weak Encryption: Using outdated algorithms like MD5 or SHA-1 that can be easily cracked.
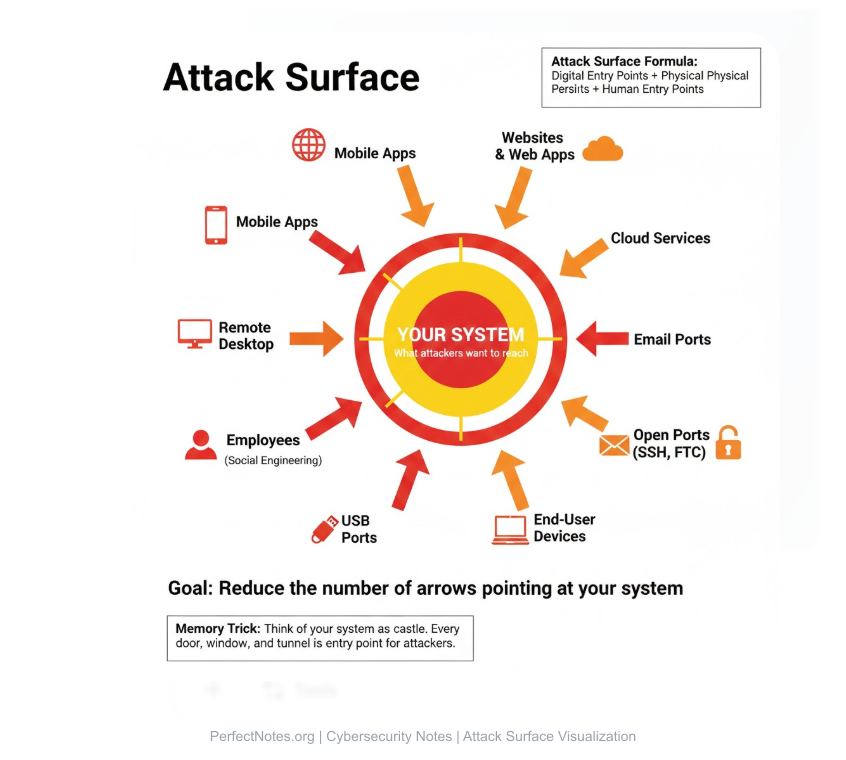
Attack Surface
The Attack Surface is the sum of all the different points (vectors) where an unauthorized user (the "attacker") can try to enter data to or extract data from an environment.
- ● Digital Surface: Ports, code, websites
- ● Physical Surface: Laptops, USB drives, server rooms
- ● Human Surface: Employees (susceptible to phishing)
Privilege Escalation:
An attacker starts with a low-level user account and exploits a bug to gain Administrator/Root access.
Code Injection:
Inserting malicious code into a computer program (e.g., SQL Injection).
Man-in-the-Middle (MitM):
The attacker secretly relays and possibly alters the communication between two parties who believe they are communicating directly.
Relationship Between Threats and Vulnerabilities
They act as two halves of a lock and key:
- ● The Threat is the burglar (the agent).
- ● The Vulnerability is the unlocked window (the mechanism).
- ● The Risk is the probability of the burglar finding the unlocked window.
Exam Tip: Removing the vulnerability (locking the window) neutralizes the threat.
.png)
Use this table to answer "Difference between..." questions:
| Feature | Threat | Vulnerability |
|---|---|---|
| Definition | A potential danger that can trigger an incident. | A weakness or flaw in the system. |
| Nature | Usually external (though can be internal). | Internal (exists within the system). |
| Control | Hard to control (you cannot stop hackers from existing). | Controllable (you can patch and fix flaws). |
| Example | A Virus, A Hacker, A Storm. | Missing Antivirus, Open Port, Weak Password. |
| Relationship | Exploits the vulnerability. | Is exploited by the threat. |
Detection & Assessment
Vulnerability Scanning
Using automated tools (like Nessus or OpenVAS) to scan a network for known flaws.
Penetration Testing
Ethical hacking where experts simulate an attack to find weaknesses before bad guys do.
Risk Assessment
Quantifying the potential impact if a vulnerability is exploited (High/Medium/Low risk).
Mitigation & Control
- ● Patch Management: Regularly updating software to fix known bugs.
- ● Secure Configuration: Changing default passwords and disabling unused ports.
- ● Network Segmentation: Dividing the network into smaller parts so if one part is breached, the others remain safe.
- ● Access Control: Implementing "Least Privilege" (users only get access to what they strictly need).
Future Challenges
As technology evolves, so do vulnerabilities. IoT devices often lack security updates, creating massive botnets. AI-driven attacks are becoming faster and smarter at finding vulnerabilities than human defenders.