Cyberspace
🔑 Key Takeaways & Definition
- ● Definition: Cyberspace is the global domain within the information environment consisting of interdependent network infrastructures, including the Internet, telecommunications, and embedded systems.
- ● Core Concept: A virtual environment without physical borders requiring cybersecurity protection.
- ● 3 Key Layers: Physical Layer, Logical Layer, and Cyber Persona Layer.
Introduction to Cyberspace
In the modern era, human interaction has expanded beyond the physical world into a digital realm known as Cyberspace. Unlike land, sea, air, or space, cyberspace is a man-made domain. It is the environment where communication over computer networks occurs. It is not just the "Internet" (which is the infrastructure); it is the experience and interaction that happens on top of that infrastructure.
Definition of Cyberspace
The term "Cyberspace" was first coined by science fiction author William Gibson in his 1984 novel Neuromancer. Today, it is legally and technically defined as the complex environment resulting from the interaction of people, software, and services on the Internet by means of technology devices and networks connected to it.
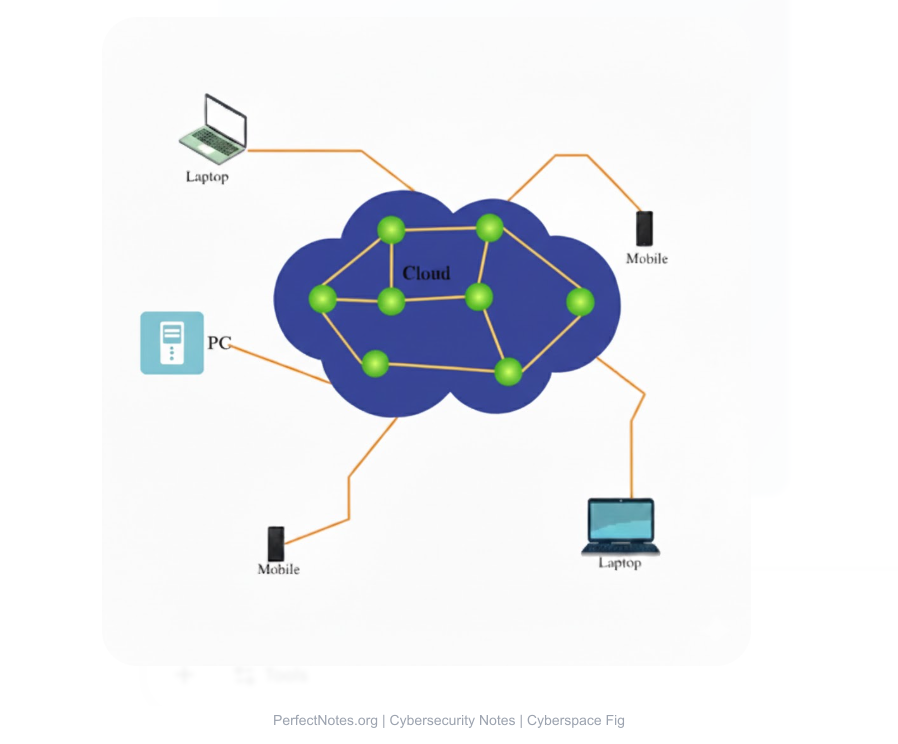
Nature of Cyberspace
Understanding the nature of cyberspace is critical for securing it.
Virtual Nature:
Cyberspace is intangible. You cannot "touch" a website or a data packet, yet they have real-world value and consequences.
Interconnected Environment:
Every device is a node in a massive web. A vulnerability in one device (e.g., a smart thermostat) can affect the security of a larger network (e.g., a power grid).
Dynamic and Evolving Space:
Cyberspace is never static. New websites are created, IP addresses change, and software is updated every second. This constant change makes security a moving target.
Characteristics of Cyberspace
- ● Borderless Environment: Cyberspace ignores geographic boundaries, creating major jurisdiction issues for cyber crimes.
- ● Dependence on Technology: It cannot exist without the underlying hardware (servers, cables, satellites).
- ● High-Speed Communication: Data travels at near light speed, allowing for real-time global interaction.
- ● Global Accessibility: Anyone with an internet connection can access it, leveling the playing field for both information sharing and malicious attacks.
- ● Scalability and Flexibility: The network can expand infinitely as more users and devices connect.
Components of Cyberspace
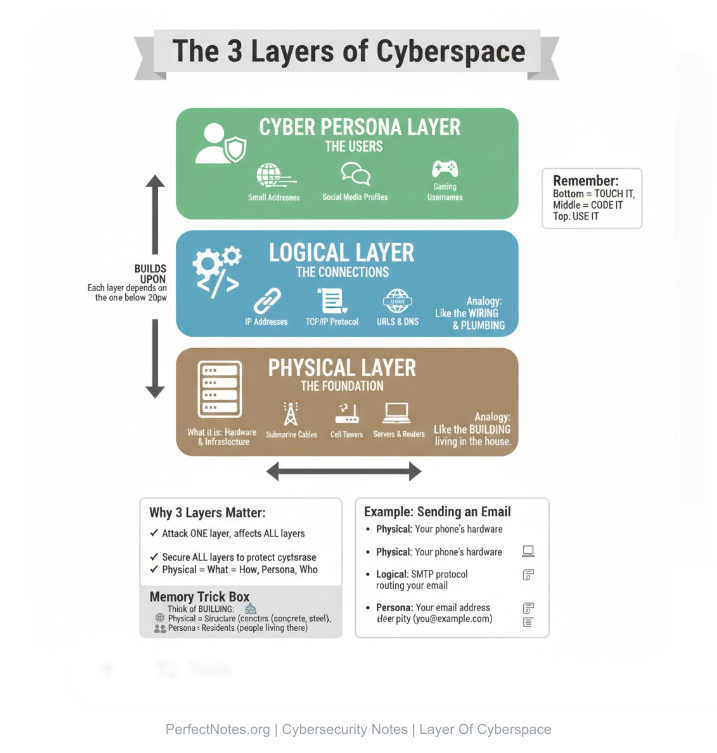
According to military and cybersecurity frameworks (like the DoD), cyberspace has three distinct layers:
| Layer | What is it? | Example | Think of it as... |
|---|---|---|---|
| Physical | Tangible hardware | Laptop, cables | The building |
| Logical | Code & protocols | IP address, HTTP | The wiring |
| Personal | User identities | Email, username | The residents |
Physical Layer:
The tangible hardware. This includes submarine cables, routers, servers, cell towers, and the user's laptop or smartphone. Without this, the other layers cannot exist.
Logical Layer:
The technical logic that drives the network. This includes IP Addresses, Protocols (TCP/IP), URLs, and software code. It connects the hardware to the user.
Cyber Personal Layer:
The identity of the users on the network. This includes email addresses, usernames, social media profiles, and digital signatures.
Note: One person can have multiple cyber personas (e.g., a work email and a personal gaming handle).
⚠️ Critical Warning: The Challenges of Cyberspace
Cyberspace introduces unique security challenges that do not exist in the physical world:
- ● Anonymity: Attackers can use proxies and VPNs to remain anonymous ("The Attribution Problem").
- ● Jurisdiction: If a hacker in Country A attacks a bank in Country B, whose laws apply? This makes prosecution difficult.
Applications of Cyberspace
- ● Communication: Email, VoIP (Zoom/Skype), and Instant Messaging.
- ● E-Commerce: Online banking (NetBanking), shopping (Amazon/Flipkart), and digital wallets.
- ● E-Learning: Virtual classrooms (like this website), MOOCs, and digital libraries.
- ● E-Governance: Paying taxes online, digital voting systems, and accessing government services.
- ● Social Media: Platforms for social interaction and content sharing (Instagram, LinkedIn).
Cyberspace vs. Physical Space
(Use this table to answer "Difference between..." questions)
| Feature | Cyberspace | Physical Space |
|---|---|---|
| Tangibility | Virtual and Intangible (Cannot be touched). | Tangible and Material (Can be touched). |
| Boundaries | Borderless and Global. | Defined by geographic/political borders. |
| Identity | Users can be anonymous or use pseudonyms. | Identity is usually tied to the physical person. |
| Distance | Irrelevant (Data travels instantly). | Relevant (Time is needed to travel). |
| Governance | Difficult to regulate (Multiple jurisdictions). | Regulated by the laws of the land. |
Cyberspace and Cybersecurity
Because cyberspace is the medium for all our data, Cybersecurity is the shield that protects it. The relationship is simple: Cyberspace is the battlefield, and Cybersecurity is the defense strategy (using Firewalls, Encryption, and Laws) to keep that battlefield safe for legitimate users.
Legal and Ethical Issues
- ● Privacy: How much data can companies collect about you?
- ● Intellectual Property: Piracy and copyright infringement are easier in cyberspace.
- ● Cybercrime: New laws (like the IT Act, 2000 in India) are needed to address crimes like hacking and cyberstalking.
Future of Cyberspace
The future includes The Metaverse (immersive VR cyberspace), IoT (billions of connected devices), and Quantum Computing (which will change how we secure cyberspace).